Discover the
Modern
WordPress with WordVell

WordPress Plugin TablePress Vulnerability Puts 700,000+ Sites at Risk
A recent vulnerability in WordPress Plugin TablePress could have exposed sites to XSS exploits, but thankfully, the team behind TablePress patched it successfully and in a timely manner.
WordPress Plugin TablePress sites are at Risk of XSS
There’s a quiet kind of trust we place in plugins. Once we click “Install,” we expect them to do their job, stay out of the way, and never betray the website we’ve worked hard to build.
So when a vulnerability is discovered in something as widely respected as TablePress, a plugin used by over 700,000 WordPress sites, it feels personal. It shakes the very foundation of how we manage trust on the backend.
But this isn’t a story about panic. It’s a reminder, a call to attention, for developers, creators, and everyone else who keeps a WordPress site alive.
What Actually Posed the Risk
According to security researchers at Patchstack,
a Cross-Site Scripting (XSS) vulnerability in TablePress version 3.2 was found. It was associated with a lesser-known parameter called
shortcode_debug
which, when mishandled, could have caused a huge security loophole and provided a safe pathway for contributors to upload malicious scripts.
What made it risky wasn’t just the flaw itself. It was the fact that someone with even Contributor-level access could use it to inject harmful scripts. In multi-author environments like blogs, online magazines, or community sites, security must be taken with even more care and focus.
To be clear: this wasn’t about hackers brute-forcing their way into your site. It was about the potential misuse of already granted access, something we often overlook until it’s too late.
The TablePress Plugin Developer Fixed the Issue, Fast
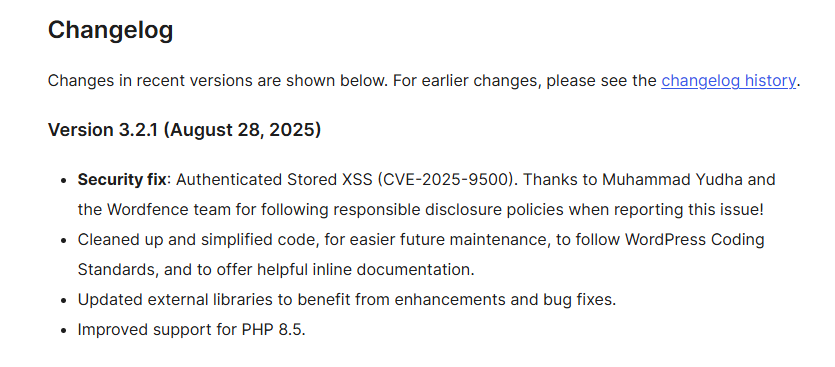
The good news is once notified, the developer of TablePress immediately released the Version 3.2.1, patching the issue by correctly sanitizing input and escaping output tied to the vulnerable parameter.
No known active exploits were reported. But don’t let the silence fool you, this was a close call, and a lucky one.
Why This Matters More Than You Might Think
This isn’t just about TablePress. It’s about the quiet assumptions we make in the way we build and manage our WordPress sites. It’s about the roles we assign to contributors, the updates we delay for “later,” and the plugins we install once and forget about.
Each incident reminds us of security as a more important aspect than we usually think.
A vulnerability doesn’t always knock loudly. Sometimes it’s subtle. Sometimes, like here, it lives in a parameter you’ve probably never touched.
Let’s Break It Down: What You Should Do Now
If TablePress is part of your stack, here’s your short checklist:
1. Check your version
Go to your WordPress dashboard → Plugins → TablePress. If you’re on 3.2 or earlier, you’re at risk.
2. Update immediately
The patch is live now. Update your plugin to version 3.2.1 or higher.
3. Audit your user roles
4. Stay proactive, not reactive
This flaw reminds us how powerful a Contributor’s role can be. Make sure only trusted individuals have publishing access, or consider limiting certain permissions altogether. Whether you’re managing five plugins or fifty, make regular plugin audits part of your workflow. Set up alerts. Enable auto-updates when it makes sense. Keep a simple changelog for your site updates.
Lessons Beyond the Code
Security is an essential aspect of safe digital products like websites or any other software. And as a WordPress developer or site owner, it’s tempting to think of security as someone else’s job something plugin authors, hosting companies, or firewalls should worry about. But the truth is, security is shared. It lives in our decisions, our user settings, and yes, our updates.
This incident with TablePress gave us another lesson that even a small mistake can pose a huge security risk.
Final Thoughts
No plugin is perfect. No stack is invincible. But being aware, informed, and responsive gives you the edge that most attackers hope you’ll ignore.
So check your version. Patch your site. And keep building with intention, clarity, and care.
Your readers may never see the work you do behind the scenes to protect them.
But that’s the point.