Discover the
Modern
WordPress with WordVell

14,000 WordPress Sites Compromised by UNC5142 Delivering EtherHiding Malware
You manage sites or build for people who run businesses. Imagine a tiny script on a trusted domain quietly delivering malware to visitors. That is the reality researchers uncovered recently.
More than 14,000 WordPress sites were compromised and used to deliver info stealing malware. The attackers hid the next stage of the attack on a public blockchain which made takedown and detection much harder. This is what happened, why it matters to developers, and exactly what to do next.
What UNC5142 Group Actually Did!
A financially motivated group tracked as UNC5142 injected a small JavaScript dropper into thousands of WordPress sites. You should know that the dropper did not host its full payload on a normal web server. Instead it pulled encoded content referenced on the BNB Smart Chain using a technique known as Ether-Hiding.
Because payload pointers live on chain defenders cannot remove them the way they would a malicious URL. The result was a resilient delivery chain for info stealing malware that targeted browser cookies credentials and crypto wallets.
Why this matters to WordPress developers
This attack is a mash up of old weaknesses and new tricks. The initial entry points were familiar: outdated plugins themes or weak configuration. The novel part is the hosting method. Storing payload references on a blockchain means the attacker can restore or update the loader without relying on a normal hosting provider.
For you this means a single compromised install can keep re-infecting visitors even after a partial cleanup. That damages, reputation SEO and client trust fast.
How the infection chain worked
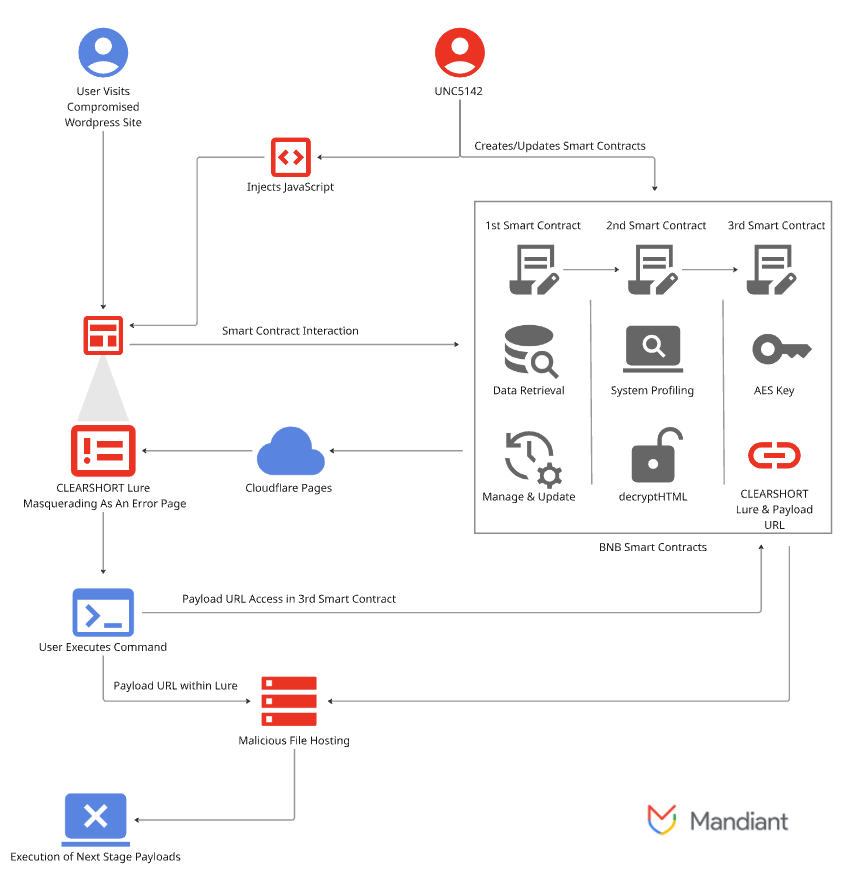
1. Attacker finds a vulnerable WordPress install.
2. A small obfuscated JavaScript dropper is injected into theme files plugin files or the database.
3. The dropper fetches encoded content referenced on the BNB Smart Chain and reconstructs a loader in the browser.
4. The loader delivers an info stealer that harvests cookies credentials or crypto wallet data or it displays a fake update prompt that tricks users into running commands.
5. The attacker collects stolen data or uses it for further compromise.
If a site shows a popup that asks users to paste commands or run terminal instructions treat that as a critical emergency. You must act immediately if you see that behavior.
Fast detection checklist for developers
Do these quick checks on any site you maintain or deploy
1. Open the site in an incognito window and look for unexpected popups fake update prompts or client side redirects.
2. Inspect the rendered HTML for unfamiliar script tags obfuscated code or hidden iframes.
3. Compare checksums of active themes and plugins with fresh copies from official sources.
4. Scan file modification times for recent unexplained changes.
5. Review server logs for odd POST requests strange user agents and repeated hits from unusual IPs.
These steps catch most client side droppers and early reinfection attempts. You can automate parts of this checklist to alert you faster.
Clean up process that works
Cleaning a compromised WordPress site is a controlled process not a guess
1. Put the site in maintenance mode and take a full backup for forensic analysis.
2. Rotate all admin FTP SFTP and API credentials immediately and force user password resets where needed.
3. Replace WordPress core and all themes and plugins with clean copies from trusted sources.
4. Search and remove injected scripts in header footer plugin files and the database.
5. Scan uploads and the configuration files for backdoors and remove or restore from a known clean backup.
6. Reissue any exposed secrets and run a full site scan with a reliable scanner.
7. Request search engine and security vendor reviews once cleanup is complete.
If the dropper referenced blockchain hosted payloads ensure you remove the dropper and any alternate backdoors before declaring the site clean.
Hardening steps to prevent reinfection
Protect all new projects with these developer focused controls
1. Enforce least privilege for accounts and restrict admin access.
2. Automate or centrally manage updates for core plugins and themes and remove unused code.
3. Add a web application firewall and file integrity monitoring with alerts on file changes.
4. Disable PHP file editing in the dashboard and apply strict file permissions.
5. Use Content Security Policy and Sub-resource Integrity where practical to limit rogue third party scripts.
6. Maintain offsite backups and test restores periodically.
7. Educate clients and editors about social engineering and never running unknown commands.
Small consistent practices stop most opportunistic attacks and raise the bar for targeted campaigns.
Final note to WordPress developers
Attackers like UNC5142 Group will combine familiar WordPress weaknesses with creative delivery methods like Ether-Hiding. Your best defense is layered and practical. Detect quickly clean thoroughly and harden consistently. As a WordPress developer, staying cautious and taking preventive steps is a must.